Cyber Security
Gap Analysis
Gap Analysis
The main purpose of gap analysis is to help organizations develop an understanding of the gaps in their performance by measuring time, money, and labor—and compare it with its target state, so that they can create effective strategies to reduce or eliminate these gaps and achieve organizational goals.
Incident Reporting and Documentation
Risk Mitigation Recommendations
Strengthening Network Defences
Compliance and Regulatory Alignment
Assessing Security Controls
Comprehensive Evaluation
Vulnerability Identification


Data Flow Structure
Data Flow Structure
We specialize in providing professional and reliable
forensics data recovery services. With our
state-of-the-art techniques and expertise, we help
individuals, businesses, and organizations recover crucial
data from a variety of digital devices, even in the most
challenging scenarios. Whether it's a deleted file,
damaged storage media, or a cybercrime investigation, our
team of skilled forensic experts is here to assist you.
Here's what sets us apart:
Data Recovery for Digital Devices
Forensic Investigations
Deleted File Recovery
Damaged Media Recovery
Cybercrime Investigation
Vulnerability Assessment
Vulnerability Assessment
With the increase of cyber threats, it is critical to defend your business's data. Identifying and responding to cyber security vulnerabilities before cybercriminals can identify and exploit them should be paramount. The online cyber-threats faced by businesses are constantly changing and with bespoke applications, multiple networks and potentially thousands of endpoints it is daunting to think of the vulnerabilities that lie within. Our Vulnerability Assessment & Scanning services help organisations identify unknown vulnerabilities in internal and external systems. We can quantify and qualify these security risks and apply the appropriate resources to re-mediate those risks in the most efficient manner. By identifying these vulnerabilities and configuration issues that hackers exploit, network attacks and compromised systems can be avoided.


Security Audit
Security Audit
A security audit, also known as a cybersecurity audit, it
is a comprehensive assessment for client organization’s
information systems; typically, this assessment measures
client's information system’s security against an audit
checklist of industry best practices, externally
established standards, and/or federal regulations.
Here's what we do:
Scoping and Planning
Information Gathering
Vulnerability Assessment
Penetration Testing
Policy and Compliance Review
Social Engineering Assessment
Physical Security Evaluation
Remediation Assistance
Ongoing Support
Reporting
System Hardening
System Hardening
System hardening is the process of allocating assets
according to security best practices to reduce their
vulnerability to cyber attacks. This process involves
reducing the "attack surface" of the content by disabling
unnecessary services, user accounts, and ports. The
purpose of system hardening is very simple.
System hardening can restore continuous work, but efforts
will pay off substantially across the organization in the
following ways: Enhanced system features - because fewer
programs and fewer features mean operational problems,
misconfigurations, and crashes . The risk of compatibility
and compromise is smaller. Dramatically improves security
Reduced attack surface means reduced risk of data leaks,
unauthorized access, system hacks or malware.
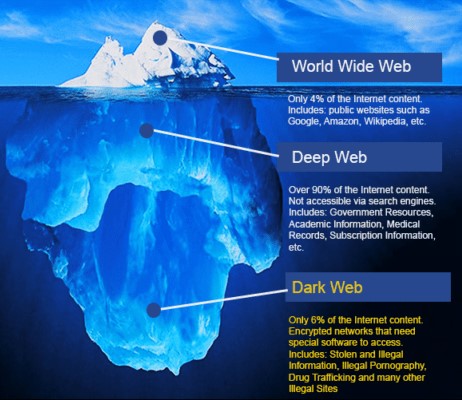
Darknet Intelligence
Darknet Intelligence
The darknet, also referred to as the dark web, is a
segment of the Internet, hidden by the novice user, that
is only accessible by using specialized software or
network proxies. Due to the inherently anonymous and
privacy-centric nature of the darknet, it facilitates a
complex ecosystem of cybercrime and illicit goods and
services trade.
Here's what we do: